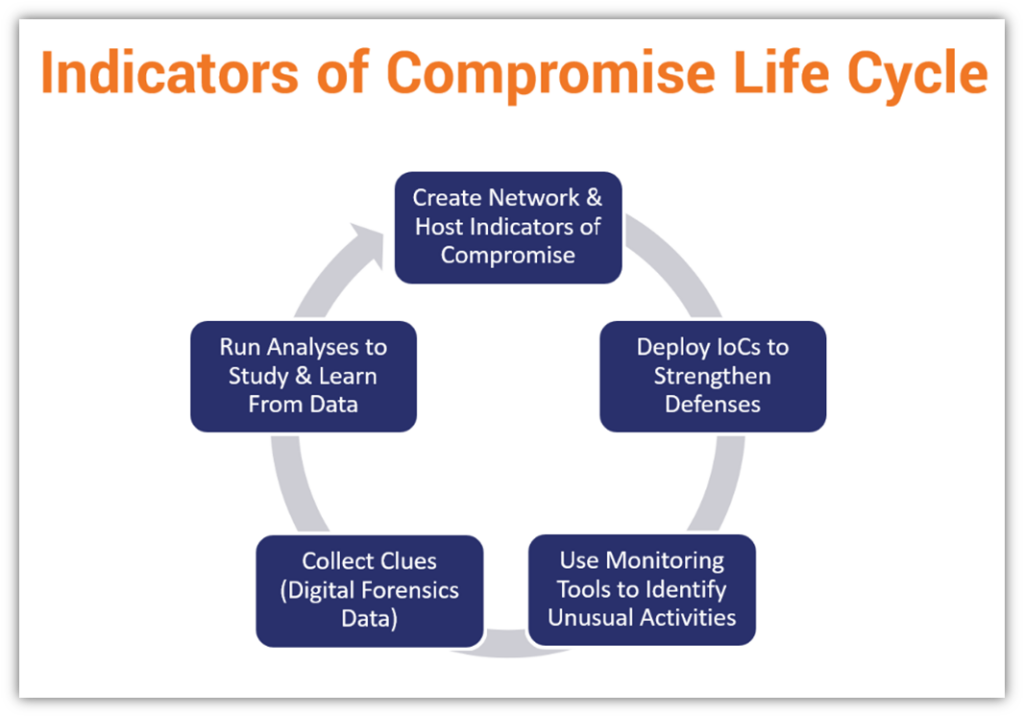
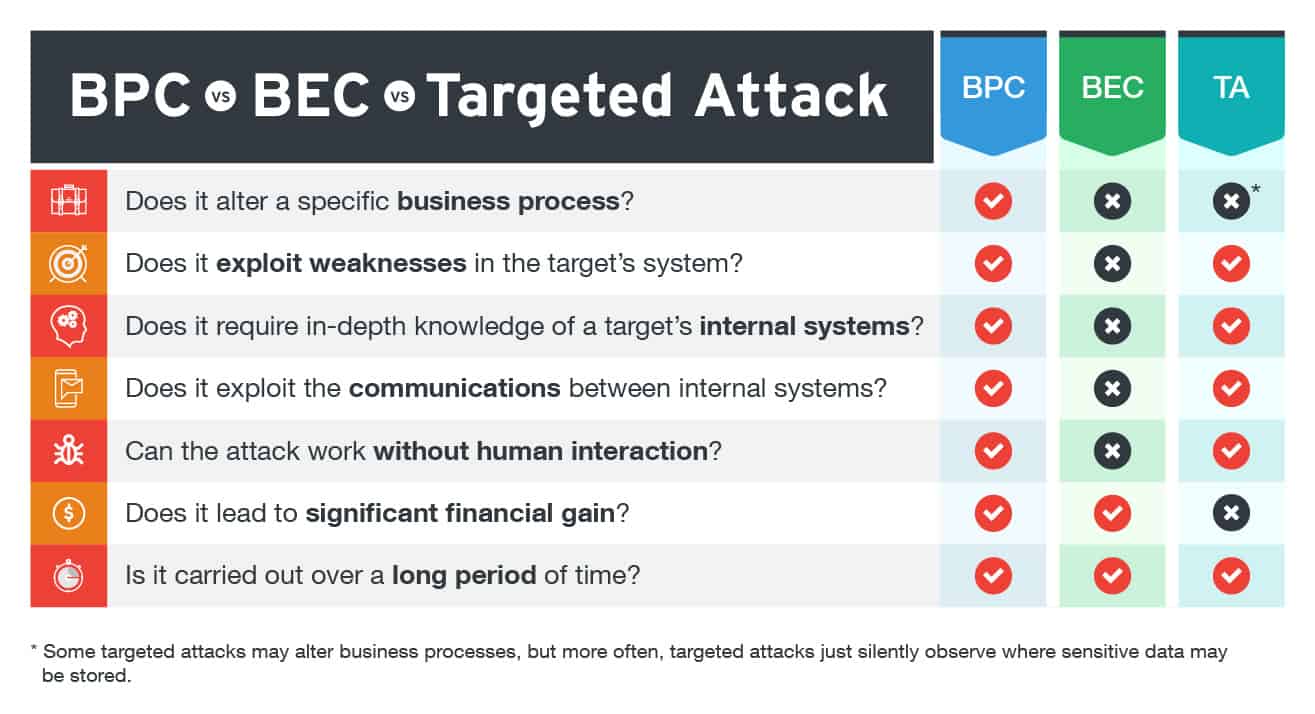
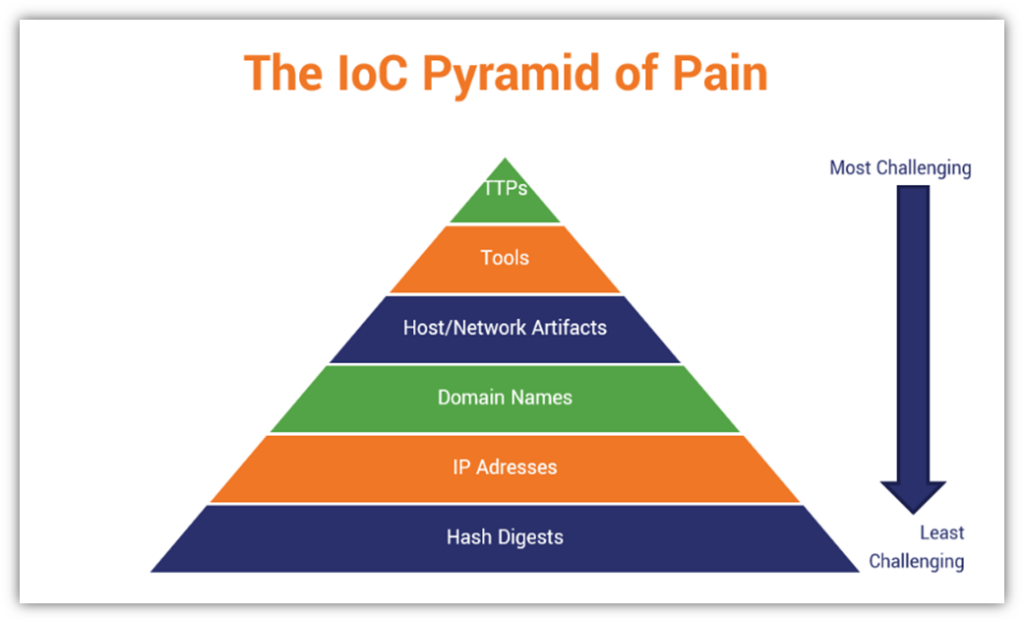
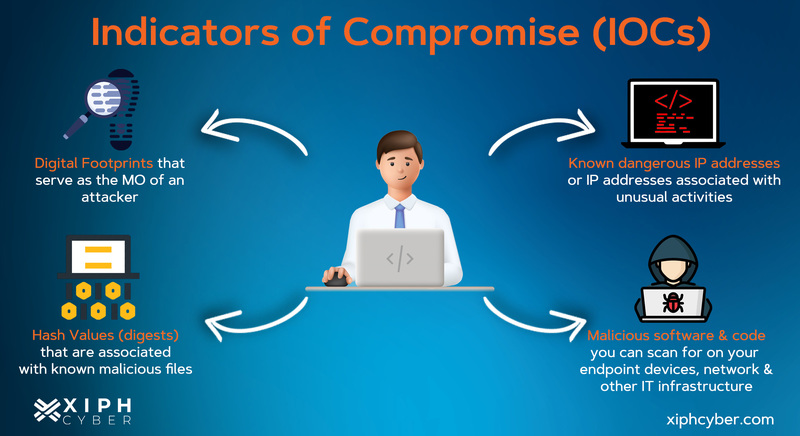
The attacker can compromise various components in a control system,... | Download Scientific Diagram

NSA, CISA: How Cyber Actors Compromise OT/ICS and How to Defend Against It > National Security Agency/Central Security Service > Press Release View

The Cavity Compromise: A sustainable system: how to integrate mite control, swarm control, honey production, and the overwintering of nucleus colonies ... and leveraging the bees' own abilities.: Quiney, Adrian, Paterson, Simon